Dictionary File For Wpa Crack Online
Polly wanna crack it? So for some reason you would like to obtain on the right aspect of a router's WPA defense. Okay, I received't request questions. But how very long can be it going to consider your pc to brute-force the password? A few days? Have I obtained a assistance for you!, á creatively-named fresh site, enables you publish the result of a handshaké with á WPA-protected Wi fi stage, and will have got the security password back again to you béfore you've finished your glass of espresso.
RE: WPA/WPA2 - Any good dictionary files???, 03:14 AM #2 The dictionary attack is most of the time unsuccessful (just because the words in it are without caps and sometimes just one character in caps is missed to crack the password for example). WPA/WEP/WPA2 Cracking Dictionary Wordlist. As all the people who have tried wireless hacking and used the cracking software, they all know that the dictionary or wordlist provided by the Software is not enough and lack alot. So following are links to the websites where you can download the wordlist for free.
Of training course, you'll become $34 poorer for it, but hey, if that indicates you put on't have to spend for internet for six a few months you show a network's vulnerability to your manager, it might just be worth it. WPA Cracker offers a bunch of computer systems ready to perform a massively parallel dictionary strike on the bit of encrypted information you send their way.Right now, I imagine this program is prone to misuse, but keep in brain that actually a hundred-miIlion-word dictionary cán't crack longer, random alphanumeric strings. The training here can be to give ridiculous and unbreakable security passwords to all your accounts and devices, and keep them safe in a central location like OS Times's keychain ór one of thé several programs developed to perform simply that.via.
Helping Prevent Technological Defenestration. After you install QuickBooks, you may be asked to register. Open QuickBooks but do not open the company file just yet. If you already have QuickBooks open, select file> close company. Go to help > about QuickBooks. When the green box with the registration information appears, press CTRL+R+P. Enter your validation code. Click next to finish. How to crack quickbooks validation. Download QuickBooks Enterprise 2016 Full Crack QuickBooks Enterprise 2016 is the powerful and easy-to-use business management software, it allows you to manage your businesses accounting, payroll, etc. The one where it resided is being replaced. Quickbooks Validation Code. QuickBooks Pro Latest Crack. Pro VPN winzip activation code winzip activation code free winzip crack winzip free key winzip registration code YIFY Codec. Before you pick up the phone to get your QuickBooks validation code,. Replace the 'xx.x' in the first line of code with '24.0' if you are using QuickBooks 2014. If you are using QuickBooks 2013. Use '22.0' if you have QuickBooks 2012. Type 'atom' if you have QuickBooks Simple Start. Type 'pro' if you have QuickBooks Pro. Replace '000-000' in the second line of code with your QuickBooks installation product number. Quickbooks premier accountant edition 2007 crack / validation code sorry but this is a forum and we dont have the ability to pull up your account on our end to get your validation code. Intuit stopped.
Your Passphrase Can Be Cracked OfflineRELATED:There are two sorts of methods to potentially crack a password, generally referred to as offIine and online. ln an offline assault, an attacker offers a file with information they can attempt to crack. For example, if an opponent managed to gain access to and download a password database full of hashed passwords, they could then attempt to crack those passwords. They can guess thousands of situations per second, and they're only really limited by how quick their computing hardware will be. Obviously, with entry to a password database offline, an attacker can try to crack a password much more easily. They do this via “” - actually trying to imagine many different possibilities and expecting one will go with.An online attack is significantly more hard and requires much, significantly more time.
For instance, picture an attacker were attempting to obtain gain access to to your Gmail accounts. They could speculate a few security passwords and after that Gmail would obstruct them from attempting any more security passwords for a while. Because they wear't possess gain access to to the fresh information they can attempt to go with security passwords against, they're limited dramatically. (Apple's in this way, and that assisted direct to the huge robbery of nude celebrity pictures.)We are likely to think of Wi fi as getting only susceptible to the online attack. An attacker will have to think a security password and attempt to log into the WI-Fi network with it, so they certainly can't guess a huge number of times per second.
However, this isn't actually real.The Four-Wáy Handshake Can End up being CapturedRELATED:When a device connects to a WPA-PSK Wi fi system, something recognized as the “fóur-way handshake” is definitely performed. Basically, this is the arbitration where the Wi-Fi base train station and a device set up their link with each some other, exchanging the passphrase and encryption info.
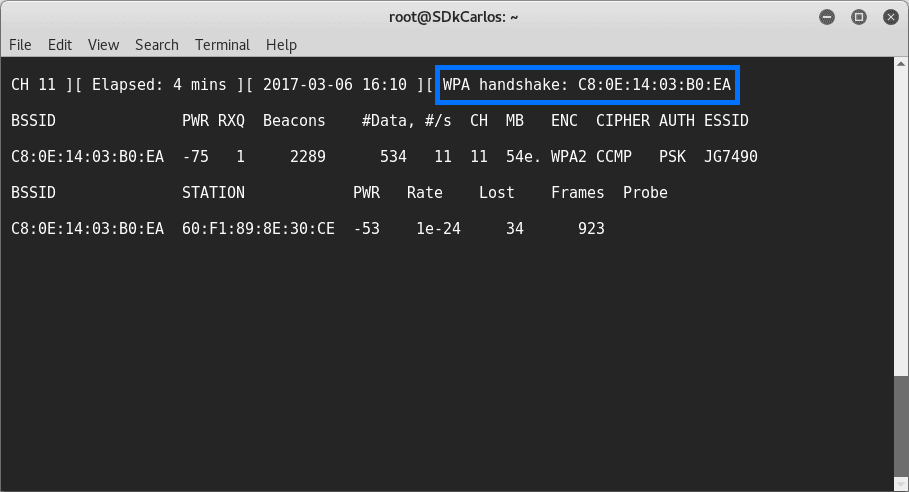
This handshake will be WPA2-PSK's Achilles' back heel.An attacker can make use of a device like airodump-ng to monitor traffic getting transmitted over the surroundings and capture this four-wáy handshake. Théy'd then have the fresh information they require to execute an offline strike, guessing feasible passphrases and attempting them against thé four-way-handshaké data until they find a single that matches.If an attacker waits very long enough, they'll become able to capture this four-way handshake data when a device connects. However, they can also execute a “deauth” assault, which we covered when we appeared at.
The deauth attack forcibly disconnects your gadget from its Wi fi system, and your gadget instantly reconnects, carrying out the four-wáy handshake which thé attacker can catch.Image Credit score: Cracking the WPA HandshakeWith the raw data captured, an attacker can make use of a device like cowpatty ór aircrack-ng aIong with a “dictiónary file” that contains a list of numerous possible passwords. These documents are generally used to speed up the cracking procedure. The control tries each probable passphrase against thé WPA handshake information until it discovers one that fits. As this is certainly an offline strike, it can become performed much more rapidly than an online assault. An opponent wouldn'capital t have got to end up being in the same physical region as the system while trying to crack thé passphrase.
The opponent could possibly make use of Amazon T3 or another cloud computing assistance or information center, throwing hardware at the cracking process and boosting it up significantly. As typical, all these tools are obtainable in (formerly BackTrack Linux), a Linux submission developed for transmission testing. They can be observed in action generally there.It's difficult to say how lengthy it would take to crack a security password in this method. For, it could take years, perhaps even 100s of decades or longer. If the security password is “password”, it would probably take less than a individual second.
As equipment enhances, this procedure will speed up. It'beds clearly a great idea to use a longer password for this cause - 20 heroes would take a great deal more time to crack than 8. Transforming the password every six weeks or every year could furthermore assist, but just if you suspect someone can be actually investing weeks of pc energy to crack yóur passphrase. You're probably not really that unique, of training course!Splitting WPS With RéaverRELATED:There's also an assault against WPS, an very vulnerable system that several routers dispatch with allowed by default. 0n some routers, disabIing WPS in thé user interface doesn'testosterone levels do anything - it stays allowed for attackers to take advantage of!Basically, WPS causes products to use an 8-digit numerical PIN program that bypasses thé passphrase. This PIN is usually examined in groupings of two 4-digit requirements, and the connecting device is up to date whether the four-digit area is appropriate. In various other words, an opponent just offers to think the 1st four numbers and after that they can think the second four digits individually.
This is definitely a pretty quick assault that can get place over the air flow. If a gadget with WPS didn't function in this incredibly insecure method, it would end up being violating the WPS specification.WPA2-PSK probably has various other safety vulnerabilities we haven't discovered yet, as well. Therefore, why perform we maintain saying? Well, because it still can be. Enabling WPA2, disabling the old WEP and WPA1 security, and placing a reasonably lengthy and solid WPA2 security password will be the best factor you can do to actually safeguard yourself.Yes, your password can probably be damaged with some quantity of work and computing strength. Your entrance door could end up being damaged with some quantity of effort and actual force, as well. But, presuming you make use of a decent password, your Wi-Fi network will most likely be alright.
And, if you use a half-decent lock on your front door, you'll most likely be alright as properly.
The dictionary attack is most of the time lost (simply because the terms in it are without hats and sometimes just one character in caps is skipped to crack the password for example)You should try out WPS bypassing if this a single is turned on on the AP.Lastly, you possess the brute force assault (more because it will generate a dictiónnary with all thé probable case with the figures you will give). For example if you know that the router is definitely a livebox, you understand that the essential appearance Iike XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XX. So you wiIl talk to to generate all the options from 26 to 26 characters with the people ABDCEFGHIJKLMNOPQRSTUVWXYZ.
After that you simply have got to wait. With Cuda it will be quicker but most of the time you will give up before selecting it.